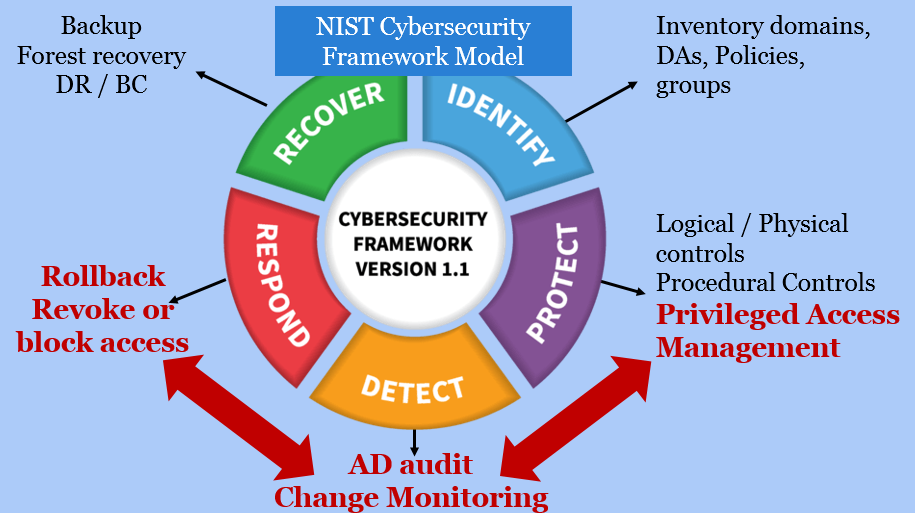
Combine Privilege Access Management (PAM) and Active Directory Audit for a Stronger Defense | BeyondTrust

CISO series: Secure your privileged administrative accounts with a phased roadmap - Microsoft Security Blog

What is Privileged Access Management (PAM)? Read the Definition in our Security Glossary | BeyondTrust