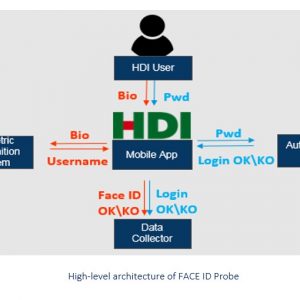
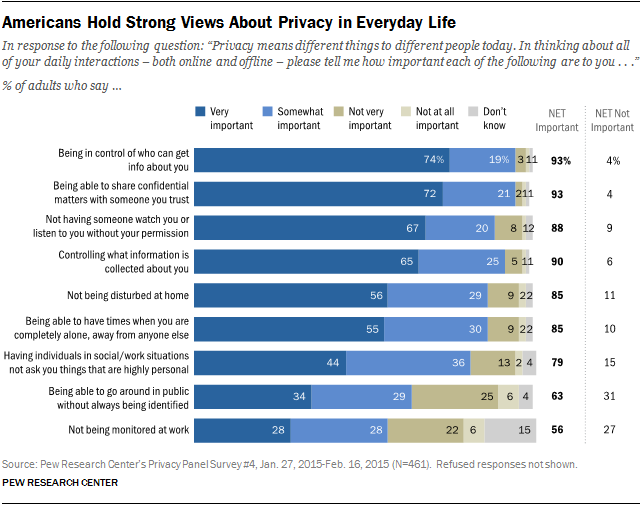
Food Security Monitoring via Mobile Data Collection and Remote Sensing: Results from the Central African Republic

Data collection and analysis tools for food security and nutrition - HLPE e-consultation on the Report's scope | High Level Panel of Experts open e-consultations
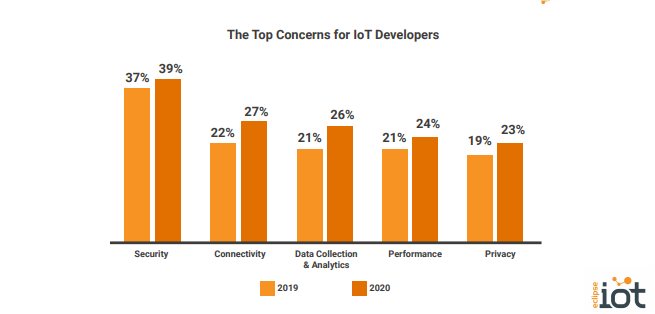
Report: Security, connectivity, and data collection remain top concerns for IoT developers - SD Times

Businesses collect more data than they can handle, only half know where sensitive data is stored - Help Net Security

Anatomy of the data collection and actuation layer—The data collection... | Download Scientific Diagram







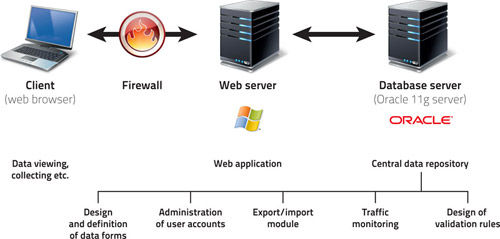

![PDF] Security Data Collection and Data Analytics in the Internet: A Survey | Semantic Scholar PDF] Security Data Collection and Data Analytics in the Internet: A Survey | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/145719a604acf9de057c60cacdea0d147cd63568/8-Figure2-1.png)